An AWS User Group Vadodara Meetup Video Fundamentals of Kubernetes on AWS EKS service
Category: AWS
AWS UG Vadodara meetup Maven Zero to Hero with AWS CodeCommit CodeArtifact ECR OWASP Dependency Track
An AWS User Group Vadodara Meetup Video on CI/CD implementation using the Maven build tool, AWS CodeCommit as a Git repository, AWS CodeArtifact as a Maven Repository, AWS ECR as a Docker repository, OWASP CycloneDx to generate a Software Bill of Material, OWASP DepencencyTrack tool for vulnerability tracking.
ACD Vadodara 2022 Microservices Observability with AWS OpenSearch
A Presentation video on implementing Microservices Observability using AWS Distro for OpenTelementry to generate trace data to send AWS DataPrepper to parse, process and send to AWS OpenSearch to index and process to generate microservices inter communication distributer tracing, provide an anomaly detection using AWS OpenSearch ML Model and application logs processing.
Event: AWS User Group Vadodara Community Day 2022
Infrastructure as Code using AWS CDK
The AWS Cloud Development Kit (AWS CDK) is an open-source software development framework that enables you to define cloud infrastructure in code and provision it using AWS CloudFormation. It provides a high-level object-oriented abstraction that enables the imperative definition of AWS resources with the help of contemporary programming languages.
With AWS CDK, you can:
- Define your infrastructure in code using a programming language you already know, such as TypeScript, Python, Java, or C#.
- Use AWS CDK constructs to represent common AWS resources and services, such as Amazon S3 buckets, Amazon EC2 instances, and AWS Lambda functions.
- Deploy your infrastructure to AWS using AWS CloudFormation.
- Automate your infrastructure deployments using CI/CD pipelines.
Here are some of the benefits of using AWS CDK:
- Consistency and repeatability: AWS CDK ensures that your infrastructure is defined consistently and can be deployed repeatedly. This makes it easier to manage your infrastructure and to track changes over time.
- Reusability: AWS CDK constructs can be reused across different projects. This makes it easier to build complex infrastructure and share your infrastructure definitions with others.
- Efficiency: AWS CDK can automate the deployment of your infrastructure. This can save you time and effort, and it can help to reduce the risk of errors.
The prerequisites for installing AWS CDK:
- Node.js 14.15.0 or later: AWS CDK uses Node.js to run its CLI and to build your infrastructure code.
- A supported programming language: AWS CDK supports TypeScript, Python, Java, and C#. You can choose the programming language that you are most familiar with.
- An AWS account: You need an AWS account to deploy your infrastructure to AWS. You can create an AWS account for free here: https://aws.amazon.com/free/.
- AWS CLI: The AWS CLI is a command-line tool that you can use to interact with AWS services. You can install the AWS CLI from the AWS CLI website: https://docs.aws.amazon.com/cli/latest/userguide/install-cliv2.html.
Node.js versions 13.0.0 through 13.6.0 are not compatible with the AWS CDK due to compatibility issues with its dependencies.
Here are some of the steps involved in using AWS CDK:
Install the AWS CDK.
npm install cdkCreate a new project.
cdk init my-cdk-project --language typescriptOnce you have created a new project, you can start defining your infrastructure in the lib/index.js file.
import * as cdk from '@aws-cdk/core';
import * as s3 from '@aws-cdk/aws-s3';
export class HelloCdkStack extends cdk.Stack {
constructor(scope: cdk.Construct, id: string, props?: cdk.StackProps) {
super(scope, id, props);
const bucket = new s3.Bucket(this, 'MyFirstBucket');
}
}Synthesize an AWS CloudFormation template for the app, as follows.
cdk synthThe cdk synth the command executes your app, which causes the resources defined in it to be translated into an AWS CloudFormation template. The displayed output of cdk synth is a YAML-format template. Following, you can see the beginning of our app’s output. The template is also saved in the cdk.out directory in JSON format.
Resources:
MyFirstBucketB8884501:
Type: AWS::S3::Bucket
Properties:
VersioningConfiguration:
Status: Enabled
UpdateReplacePolicy: Retain
DeletionPolicy: Retain
Metadata:...As with cdk synth, you don’t need to specify the name of the stack since there’s only one in the app.
Deploy your infrastructure to AWS.
cdk deploy cdk deploy displays progress information as your stack is deployed. When it’s done, the command prompt reappears. You can go to the AWS CloudFormation console and see that it now lists HelloCdkStack. You’ll also find MyFirstBucket in the Amazon S3 console.
Maven Zero to Hero with AWS CodeCommit CodeArtifact ECR OWASP Dependency Track
A Presentation on CI/CD implementation using the Maven build tool, AWS CodeCommit as a Git repository, AWS CodeArtifact as a Maven Repository, AWS ECR as a Docker repository, OWASP CycloneDx to generate a Software Bill of Material, OWASP DepencencyTrack tool for vulnerability tracking.
Manage AWS Account Using IAM Identity Center or AWS Single Sign On
AWS IAM Identity Center is a cloud-based identity and access management (IAM) service that helps you manage your users and their access to AWS accounts and applications. It provides a single place to create, connect, and manage your workforce users, and to centrally manage their access across all your AWS accounts and applications.
AWS Identity Center (IAM Identity Center) is a service that makes it easy for you to centrally manage access to multiple AWS accounts and business applications. It provides your workforce with single sign-on access to all assigned accounts and applications from one place.
Here are some of the benefits of using AWS IAM Identity Center:
- Centralized access management: IAM Identity Center allows you to centrally manage access to all your AWS accounts and applications from a single console. This makes it easy to track who has access to what, and to revoke access as needed.
- Single sign-on: IAM Identity Center provides single sign-on (SSO) for all your AWS accounts and applications. This means that your users can sign in once to IAM Identity Center and then access all their assigned accounts and applications without having to enter their credentials again.
- Fine-grained permissions: IAM Identity Center allows you to define fine-grained permissions for your users. This means that you can control exactly what resources your users can access and what actions they can perform.
- Auditing and reporting: IAM Identity Center provides auditing and reporting capabilities. This allows you to track user activity and to identify potential security risks.
- Integration with other AWS services: IAM Identity Center integrates with other AWS services, such as AWS CloudTrail and AWS Security Hub. This allows you to get a comprehensive view of your AWS security posture.
Overall, AWS IAM Identity Center is a powerful tool that can help you to improve the security and efficiency of your AWS environment.
Here are some additional benefits of using IAM Identity Center:
- Reduced administrative overhead: IAM Identity Center can help you to reduce the administrative overhead of managing access to multiple AWS accounts and applications. This is because IAM Identity Center can automate many of the tasks that are involved in managing access, such as provisioning users, assigning permissions, and revoking access.
- Improved security: IAM Identity Center can help you to improve the security of your AWS environment by providing centralized access control and auditing capabilities. This can help you to prevent unauthorized access to your AWS resources and to identify and respond to security incidents more quickly.
- Increased compliance: IAM Identity Center can help you to demonstrate compliance with industry regulations such as HIPAA, PCI DSS, and GDPR. This is because IAM Identity Center provides auditing and reporting capabilities that can help you to track user activity and to identify potential security risks.
If you are looking for a way to centrally manage access to multiple AWS accounts and applications, then IAM Identity Center is a good option to consider. IAM Identity Center can help you to improve the security, efficiency, and compliance of your AWS environment.
AWS IAM Identity center was knows as AWS Single Sign-On (AWS SSO) service.
Start AWS IAM Identity center setup by opening a IAM Identity center dashboard page. (search from service search bar)
Open Identity Center Dashboard to enable the IAM Identity Center

If AWS Organization is not enabled and set this process also would ask for enable and set AWS Organization with IAM Identity center enable process.
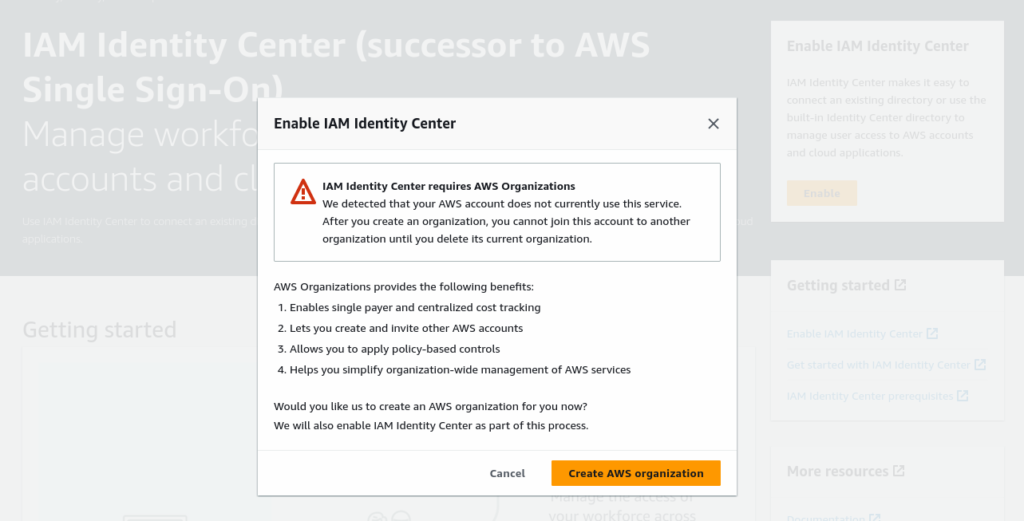
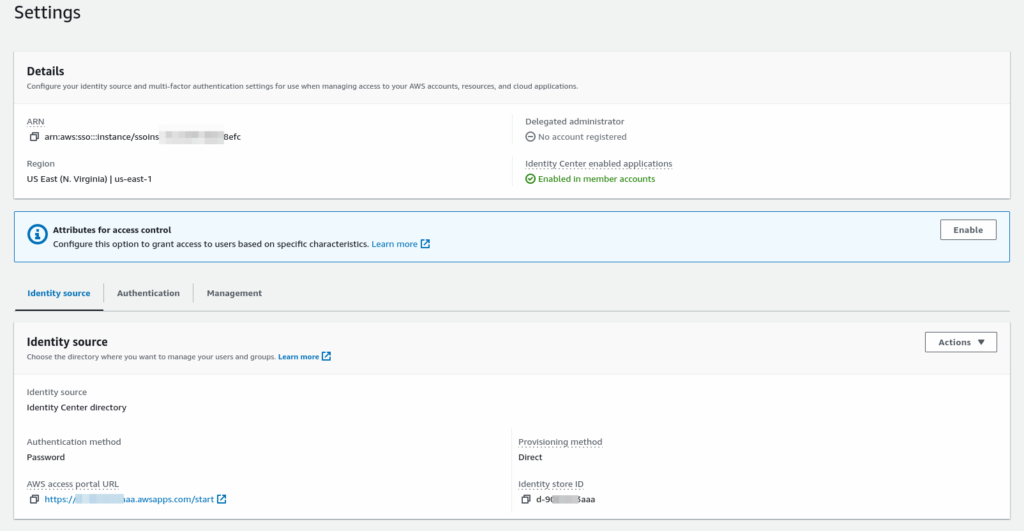
Once AWS Organization is created and IAM Identity center is enabled, you are good to start setting IAM Identity center to create a user and provide permission to login into AWS Account also it allows you to federate Users with a Directory provider like Active Directory. In the Settings Summary, you can find the “AWS Access portal URL” This is the URL going to be used for login into AWS Account using IAM Identity center.
AWS Access portal url: https://xxxxxxxxaaa.awsapps.com/start
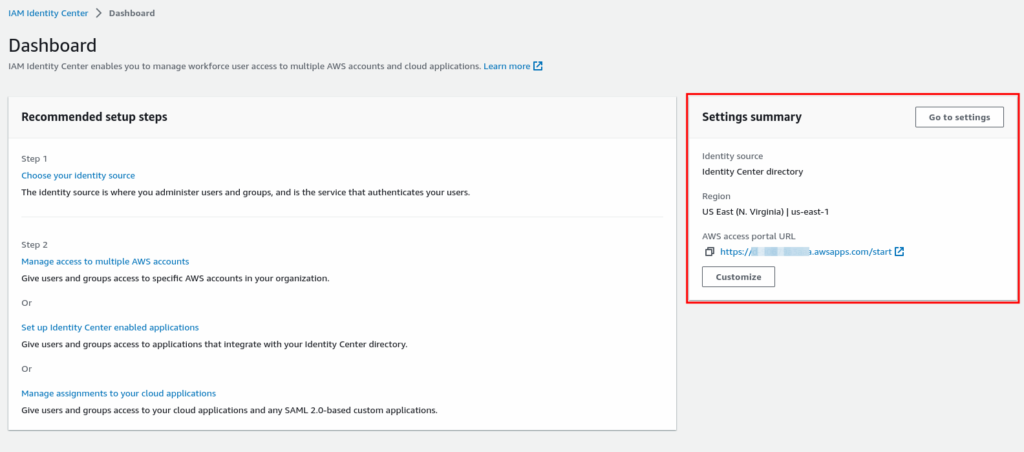
The Dashboard shows the Recommend setup steps to follow.
Step 1: Choose your identity source
Nothing needs to do unless you plan to use other identity stores then
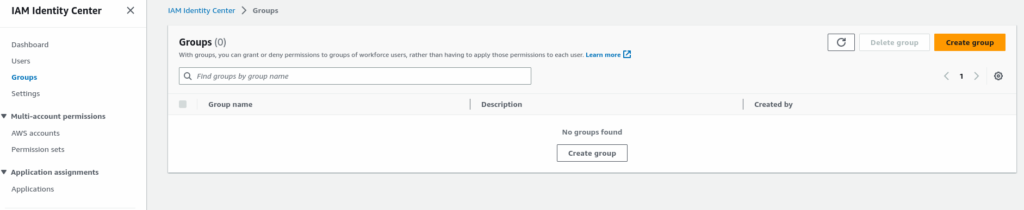
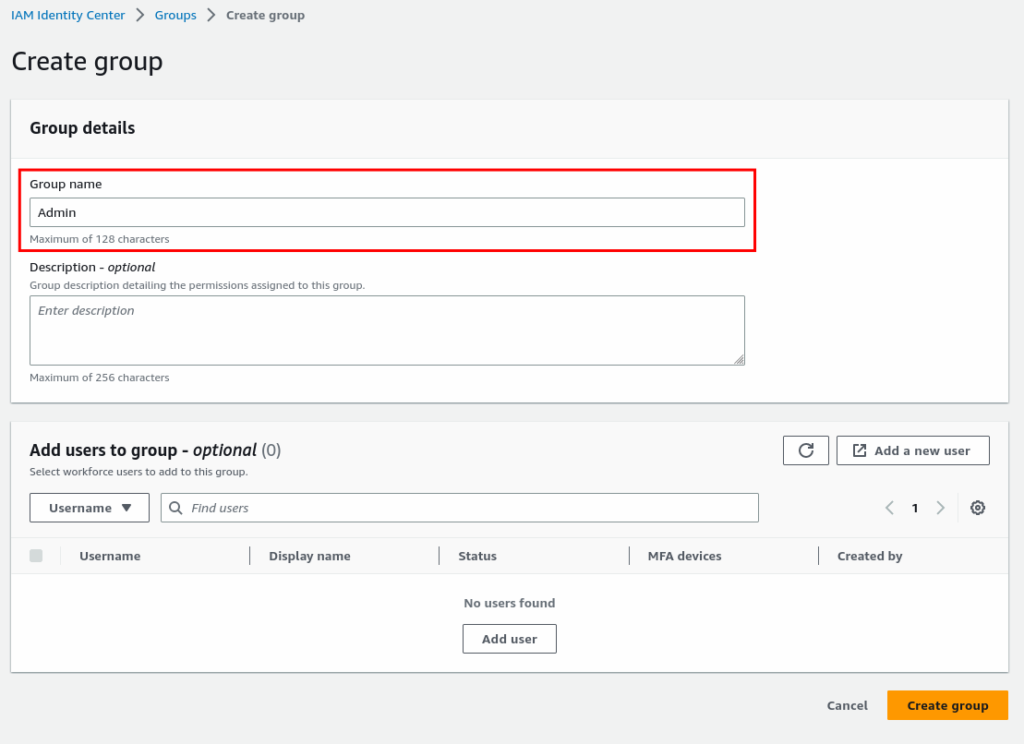
Step 2: Create a Group and assign an permission
Create Group
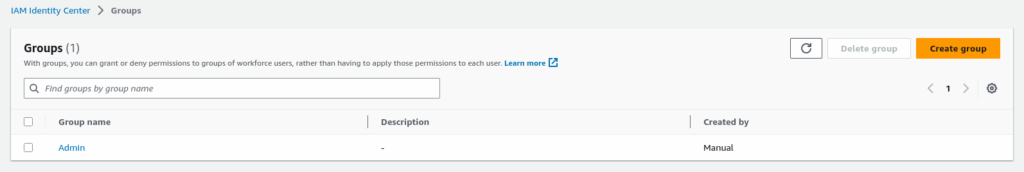
Display List Crated Group
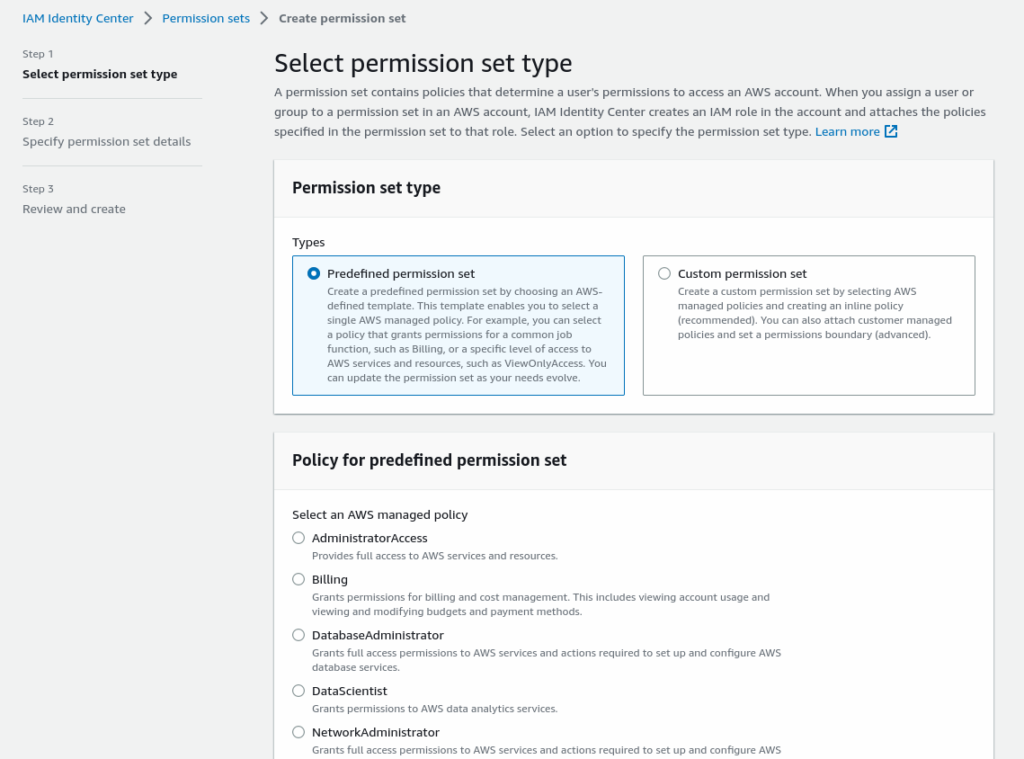
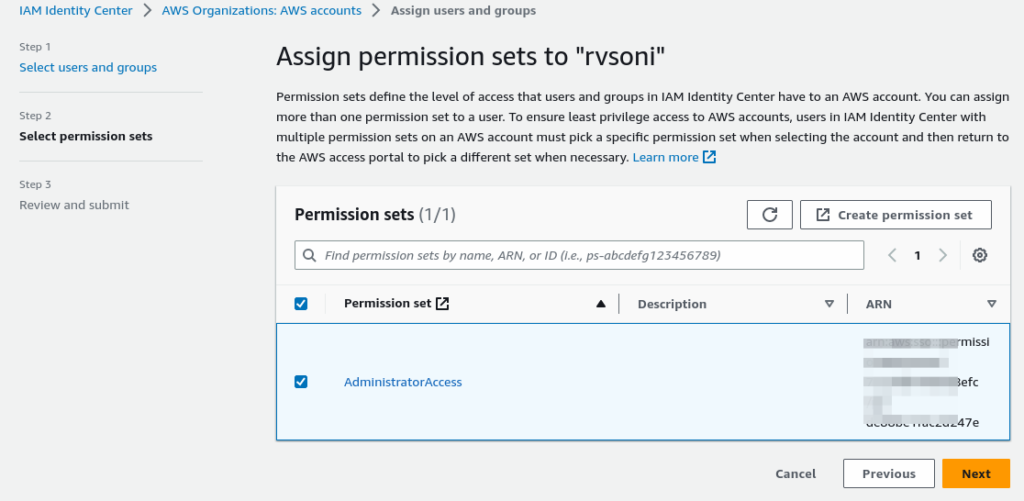
Step 3: Create a permission set by Policy for predefined permission set or create Custom permission set and assign to Group
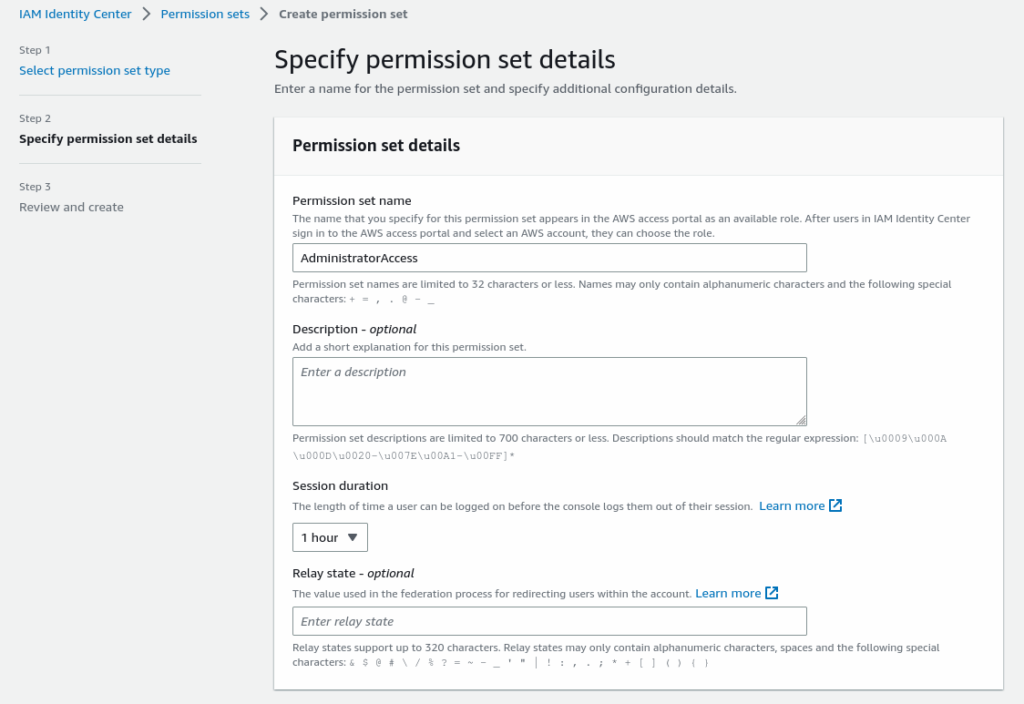
Select AdministratorAccess from select an AWS Managed policy and click Next to set a detailed setting like session timeout.
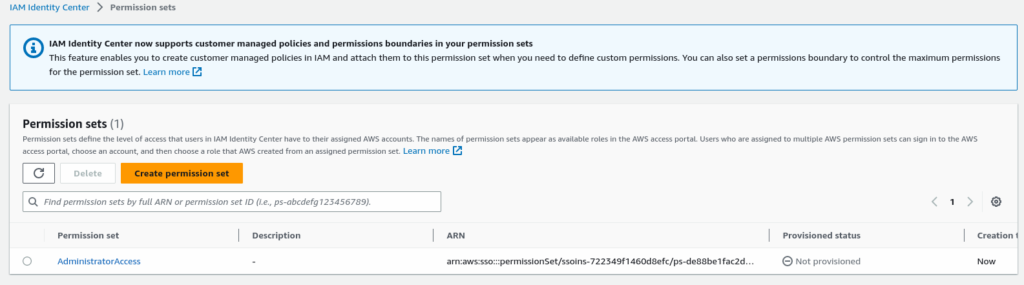
Review and create a permission set.
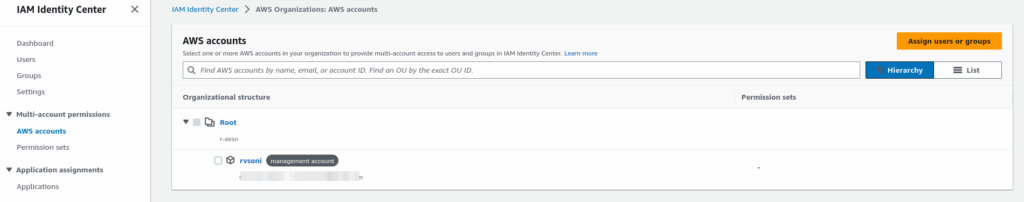
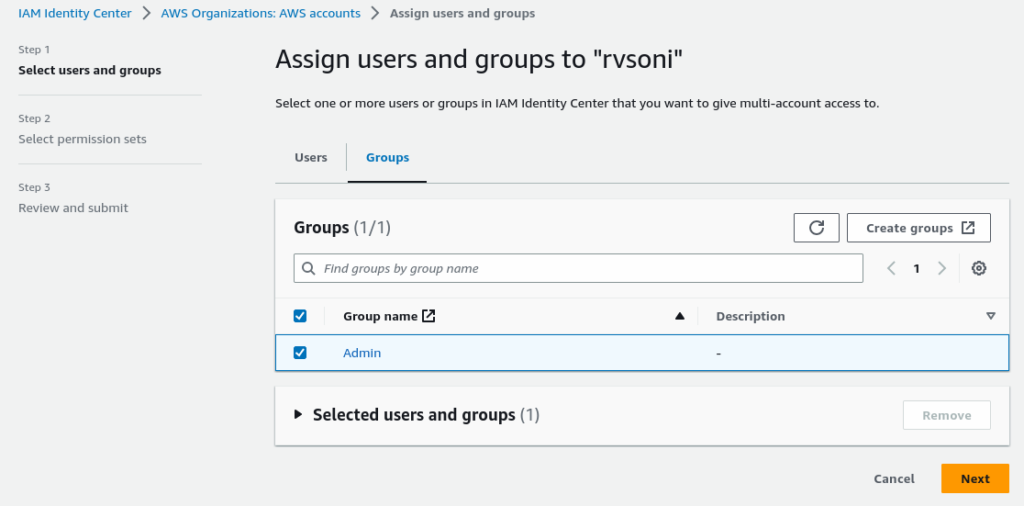
Now it’s time to associate Account with permission set and group. For this select Account from AWS Organization
Select a Group from the list of groups to associate with Account
Select Permission set from a list of permissions
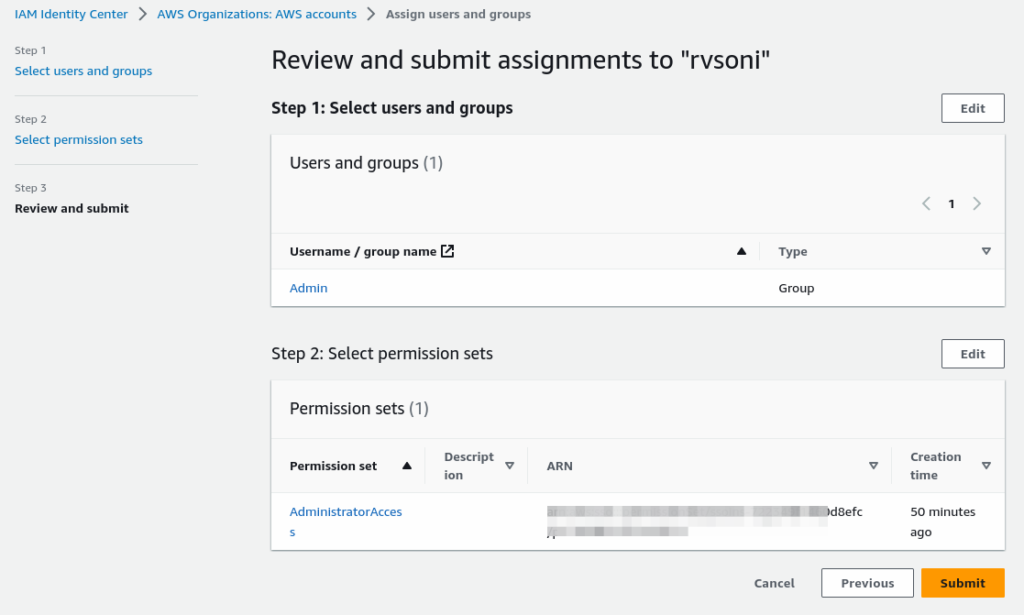
Review and submit to associate Account, Group, and Permission set.
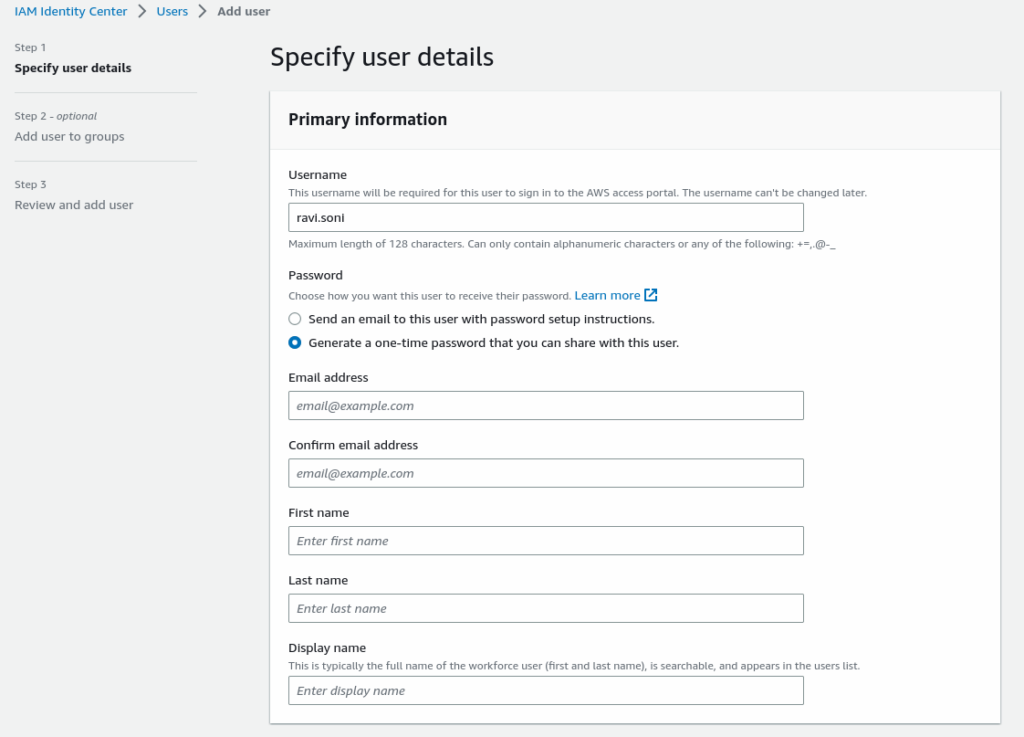
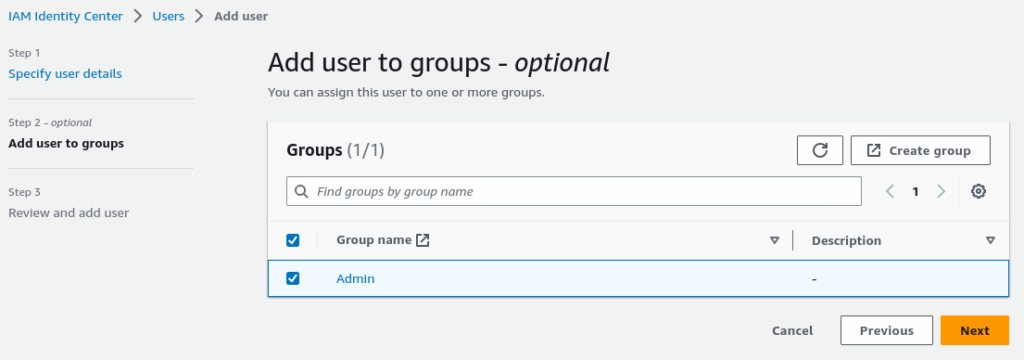
Now Account, Group, and Permission Set the time to create a User with an email address, Name and add to the Admin group.
Select Admin Group from the group list
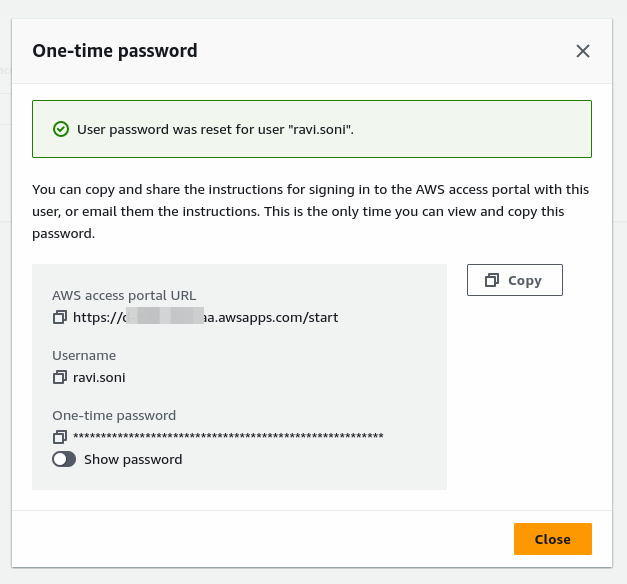
Review and Add the user. this would one-time password and login detail.
Now AWS IAM Identity Center is ready to log in. Open AWS Access portal URL to log in using the user and reset the password.
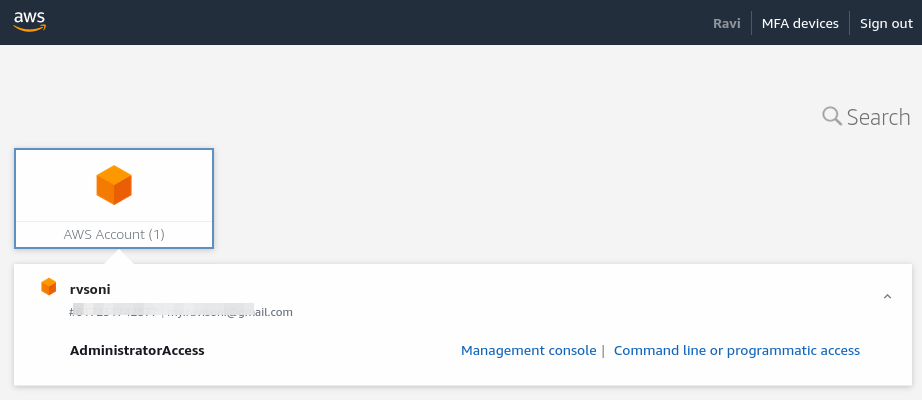
Once login into AWS Portal, you can select AWS Account and log in by assuming Admin Role or can get a Setting for AWS Cli configuration to use AWS Cli (V2) using AWS SSO.
Click on “Command line or programmatic access” would open a popup to show the AWS SSO tokens details and the way to configure AWS Cli (V2) using AWS SSO

Happy AWSing!
Microservices Observability with AWS OpenSearch AWS Distro for OpenTelemetry and Data Prepper
A Presentation on implementing Microservices Observability using AWS Distro for OpenTelementry to generate trace data to send AWS DataPrepper to parse, process and send to AWS OpenSearch to index and process to generate microservices inter communication distributer tracing, provide an anomaly detection using AWS OpenSearch ML Model and application logs processing.